Tldr: Someone can guess reasonably where you are by sending you a glitched friend request notification on your phone that tells the hacker what data center you’re closest to.
It is pretty clever but I wouldn’t call it full deanonymizing, should still get patched though.
good find by the tester.
Edit: used the term ‘glitch’ for simplicity of people reading, didn’t mean to upset people; I’m just an amateur.
It’s not a glitched friend request notification.
It’s a native friend request that you make through discord. The vulnerability lies in the attacker making a unique pfp for each request, forcing the CDN to cache the pfp at the closest data center to the user.
I would agree that it’s not fully deanonymizing but it could resurrect tracking Elon and other billionaires.
I like how you see the positive in bad news 😃
Don’t we lnow wjere to shoot down their planes alreqdy? Or wait until they bribe washington officials?
It’s not even glitched, it’s working as intended
deleted by creator
Was posted yesterday to a lot of communities, it’s very clickbait:
allows an attacker to grab the location of any target within a 250 mile radius
So it’s a bit rough… In Europe it means basically which country the target is in. Also cloudflare servers are not evenly distributed in the world, so resolution can differ wildly worldwide.
With a vulnerable app installed on a target’s phone
So it’s not really zero click.
Sounds interesting though, nice writeup, but not as scary as it sounds from the title.
The vulnerable app can be anything that displays an attached image though. And a 250-mile radius compared to the whole world is still a very significant step for governments trying to track down dissidents, etc.
The section on responses by Cloudflare, Signal and Discord is disappointing. They’re not taking it seriously enough.
so it’s not really zero click
Did you keep reading after the intro?
Excerpt:
If the target has push notifications enabled (which it is by default), they don’t even have to open the Signal conversation for their device to download the attachment. Once the push notification is sent to their device, it automatically downloads the image from Signal’s CDN triggering the local datacenter to cache the response.
An attacker can run this deanonymization attack any time and grab a user’s current location without a single interaction.
If it’s still only the datacenter it doesnt matter that much.
GeoGuesser, powered by the Google Maps API, generates a likely location of the user. It finds the midpoint between the 2 datacenters and draws 2 circles that signify his radius.
And with SS7 they can get even more precise location, and you can’t really hide from that if you want to use a phone with a phone number, what is the point. This is an interesting way of attack, noone really thought about this before, but it’s not “oh-my-god everyone can be tracked via signal”. I guess the closest server doesn’t even selected via geographical distance, but much more depends on network infrastructure of your location, so Google Maps API can’t really help here.
And again any VPN could defend against this, so if you want to hide which country you are in currently, it should be the 0th step to use a VPN.
Does everyone have access to tracking which stations send the phone signal in the SS7 network?
Yes, anyone can buy access.
Cloudflare has more servers in Europe than in North America. That does trace you to which country, which IMO is pretty significant. Especially with the GeoGuesser “average the circles” thing he coded.
The user having to have the vulnerable app installed does not make it not zero click.
My favorite part might be the conversation on the Cloudflare forum where a user reports the bug that makes this possible and it ends with this:
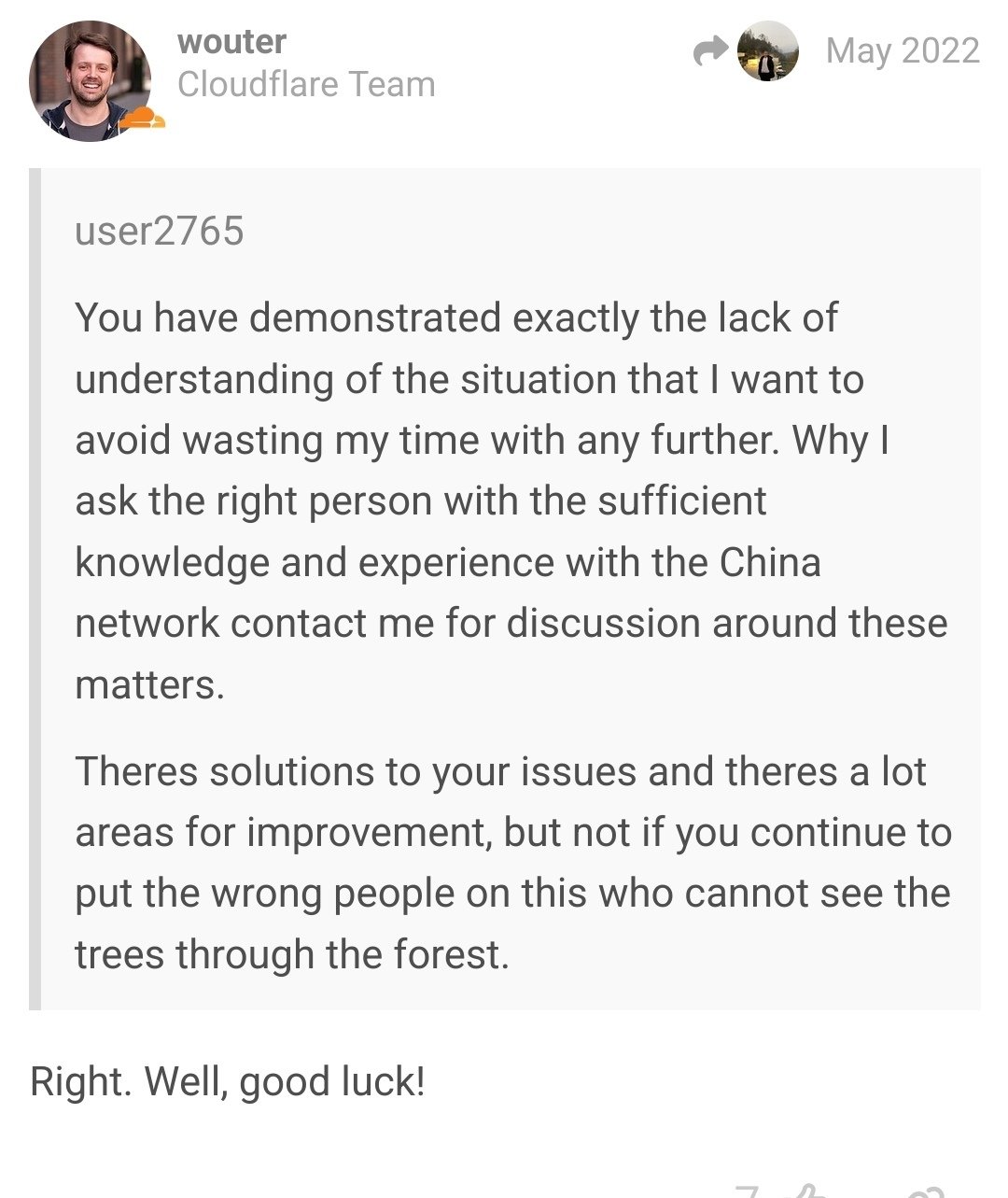
😂
Interesting read. One thing I don’t fully get is why does Cloudflare have the airport code in the response headers anyway? I cannot think of a single reason to have it in the response.
They use airport codes for their data center identifiers.
Yeah I get that, but why return that information in the HTTP response?
That’s a pretty clever trick.
deleted by creator
You need to up your game I can almost understand that title.
I don’t get it?
Why not just sending someone a link to an image on your website? You grab the IP address and are probably closer to the actual location with less work. Or would Signal proxy the image? Then, you need to just send a link. The user clicks (1 click attack) and you get the IP address…
Most platforms proxy media shared.
Then your proposed workaround is still 1 click more than the reported one.
yes, ok, but the 0 click reveals that I’m probably living in Germany (I just kind of doxed myself) and the IP can reveal the city or village I’m living in and if you cantact my ISP as law enforcement, you could probably find out my name and address…
But ok, the post is probably a bit of clickbait, because you can’t do much with the information you get from this method.










