

The only downside to using one today is that it charges via mini USB. Not USB C like a PS5 controller, or even micro USB like a PS4 controller. It uses mini USB like a PS3 controller.
Please correct my English.
The lemming formerly known as:


The only downside to using one today is that it charges via mini USB. Not USB C like a PS5 controller, or even micro USB like a PS4 controller. It uses mini USB like a PS3 controller.


Can’t wait to see what they come up with next.
Framework smartphone please. Though I think that is VERY unlikely.


Lemmy seemed to parse that as two separate hyperlinks for me. This should work as a simple clickable link 🤞 https://web.archive.org/web/20240926051545/https://forum.makemkv.com/forum/viewtopic.php?f=16&t=19634


Is it just me, or are filters not working?
EDIT: I just removed one of my filters, added it again, and now all my filters are working as expected.


Hmm, I think this is an Mbin vs Lemmy issue. There are two differences in the URL:
%2C instead of ,. This part does not make a difference, because that resolves to a comma anyway= at the very end for some reason. This is what breaks it. Remove that character, and the URL works fineThe weird thing here is that the broken URL only ever shows up on Mbin. Below are a few different links to the comment in which you shared the broken URL. If you view the comment on your Mbin instance, it is indeed broken. But if you view it on this community’s Lemmy instance or my home instance, your same comment actually has the working URL. Something about how the post/comment were federated must have messed things up.


Is that not literally the same link as the OP?
EDIT: Ah, the OP’s edit from 30 minutes before your comment has not federated out to your instance yet.
It doesn’t make sense. I understand it, but it doesn’t make sense.
Are you just referring to how Python uses the English and/or instead of the more common &&/||? I think what the user above you was talking about was Lua’s strange ternary syntax using and/or.


A little less formal than an e-mails.


The comments below started me on a trail that led me to a relevant comment from a Lemmy dev:
I want to remind everyone that since users overwhelmingly don’t want their votes snooped on (for good reason), we will never add anything like this inside lemmy, lemmy-ui, or jerboa.


But it’s trivial to use an external tool to see who voted on what regardless of whose account it is
Is there a tool made for this out there? As far as I’m aware, the simplest way for the average user to do that is to run their own instance and then manually query its database directly, which is far from trivial.


This article does clearly state that both prices are USD, but everywhere else indicates that the price is 1000 CAD.
There doesn’t need to be any evidence. This is something that is impossible to prove one way or the other, like Last Thursdayism.
Yes, this particular incident.
https://en.wikipedia.org/wiki/XZ_Utils_backdoor
In February 2024, a malicious backdoor was introduced to the Linux build of the xz utility within the liblzma library in versions 5.6.0 and 5.6.1 by an account using the name “Jia Tan”.[b][4] The backdoor gives an attacker who possesses a specific Ed448 private key remote code execution through OpenSSH on the affected Linux system. The issue has been given the Common Vulnerabilities and Exposures number CVE-2024-3094 and has been assigned a CVSS score of 10.0, the highest possible score.[5]
Microsoft employee and PostgreSQL developer Andres Freund reported the backdoor after investigating a performance regression in Debian Sid.[8] Freund noticed that SSH connections were generating an unexpectedly high amount of CPU usage as well as causing errors in Valgrind,[9] a memory debugging tool.[10]


Immediately get noticed
Realistically, though, we are only aware of that one because it was noticed in that unlikely scenario and then widely reported. For all we know, most open source backdoors are alive and well in our computers, having gone unnoticed for years.
For when you want to delete everything in the root directory, but absolutely need to keep the directory itself.
You can open me in Vim, Greg. Am I a file?
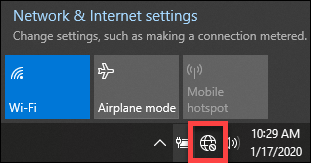
Also the internet icon shows there is Internet.
Looks to me like the icon that indicates the machine being connected to a network, but that network is not connected to the Internet.


Which GitHub version?
The culture of things that are not inherently political?